The file first seen on 2/11/2021
Malware Bazaar Source: https://bazaar.abuse.ch/sample/5134951dfe74a2803ae255e7ba55e765fb16b1f212ecaa957aa612e304423ecd/
Malware Bazaar Download: https://bazaar.abuse.ch/download/5134951dfe74a2803ae255e7ba55e765fb16b1f212ecaa957aa612e304423ecd/
Any.Run Link: https://app.any.run/tasks/5f9b8d93-c044-4847-a30e-474f6ad98955/
I won’t go over how to unzip or rename a file this time, if you have been following along from the beginning I provided the commands to unzip and rename the file.
Once we have the files unzipped, I will use “OLEVBA” to see if I can identify any suspicious code.
Command: olevba hancitor.doc
There was a lot of VB script code that was displayed, but I here is an output of the summary.

I am going to extract the hancitor.doc to a directory.
Command: unzip hancitor.doc -d media
I will take a look at the file “vbaProject.bin” and see if there is anything interesting in that file….
Command: strings media/word/vbaProject.bin | more
Nothing that is easily understandable.. Booo…
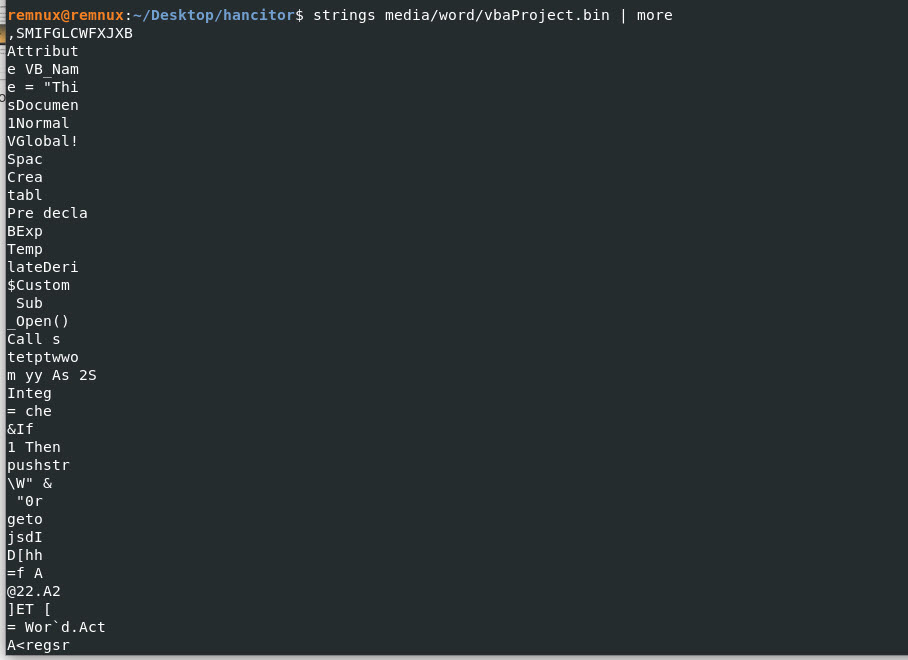
Looking at the “oleObject1.bin” file it looks like I might have stumbled over some executable code, potentially..
Command: strings media/word/embeddings/oleObject1.bin | more
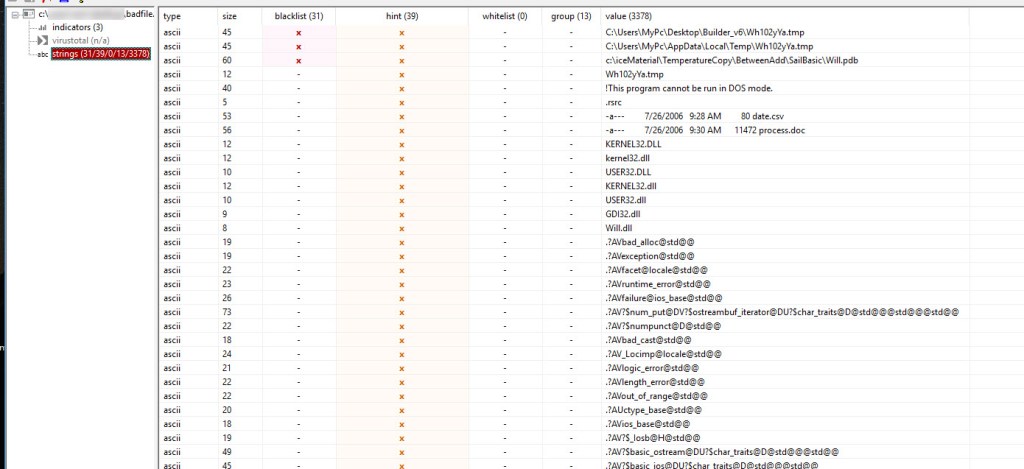
The yellow box is showing what could be some indicators that we can potentially look for within the environment.
The red arrow shows us the famous “This program cannot be run in DOS mode.” indicating there could be a potentially executable embedded in the document or something to throw off our analysis.
Looking for HTTP string information did not provide anything useful.
Command: strings media/word/embeddings/oleObject1.bin | grep http
I am going to use “Oledump.py” to see if there is any good information within the “vbaProject.bin” file.
Command: oledump.py /media/word/vbaProject.bin
Nothing useful… I am going to move on the next file “oleObject1.bin”
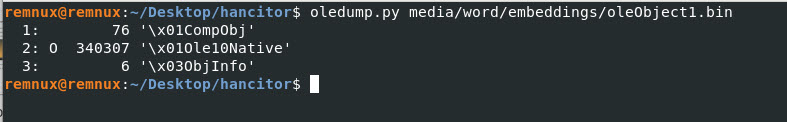
Command: oledump.py media/word/embeddings/oleObject1.bin
Here I found something, but I have to dig deeper to see if the information provided is useful for our investigation.
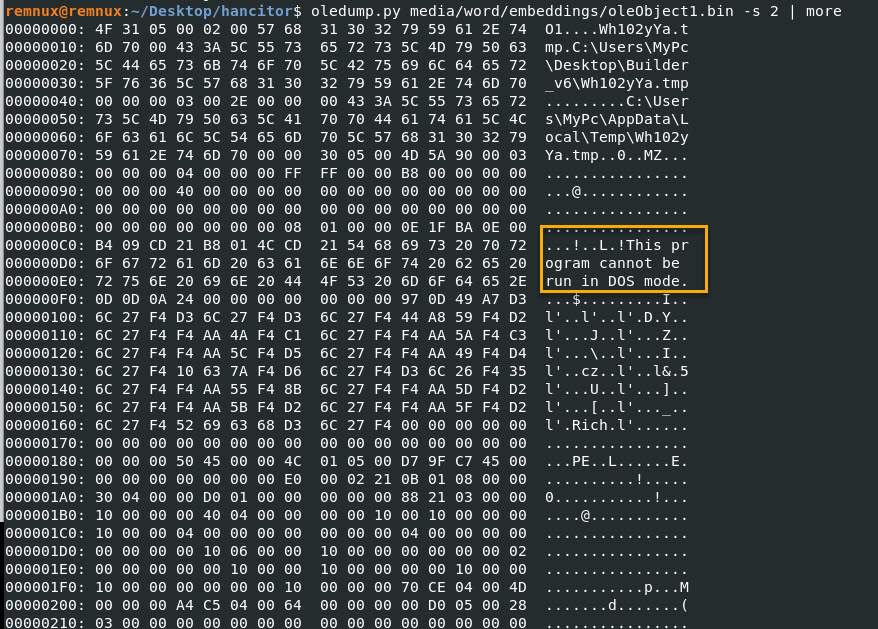
I will take a look at section 2 and output the pipe the information to the more command.
Command: oledump.py media/word/embeddings/oleObject1.bin -s 2 | more
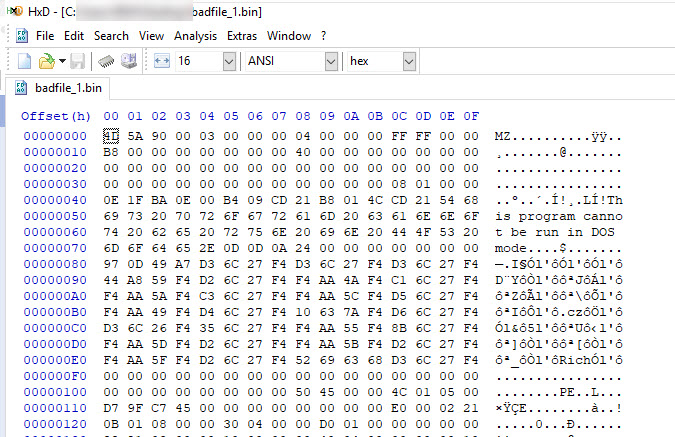
There must be an executable embedded in this document, because I keep seeing “This program cannot be run in DOS mode.” with the magic number which is “MZ”
I am going to output this data into a “.bin” file and see what happens…when I run the file command against my output.
Command: oledump.py media/word/embeddings/oleObject1.bin -s 2 -d > badfile.bin
Once the file has been created I will run the file command to see if the data is being read as regular text or data.

Perfect… I will copy the file over to a Windows machine to modify it a little bit with the tool “HxD”.
When I open the file with PeStudio I am unable to see any real useful information. I see calls to DLLs and some readable strings but it doesn’t look like your normal malicious executable, showing you import table info, etc.
Now I will take a look at the file using the “HxD” tool…
Normal executable files start of with magic byte of “MZ” as you can see below, the file does not start with “MZ”.
I will delete what I don’t need and save the file to a badfile_1.bin and upload to PeStudio.
Before… we are going to get rid of the information highlighted.

After…. And I will save the file as badfile_1.bin
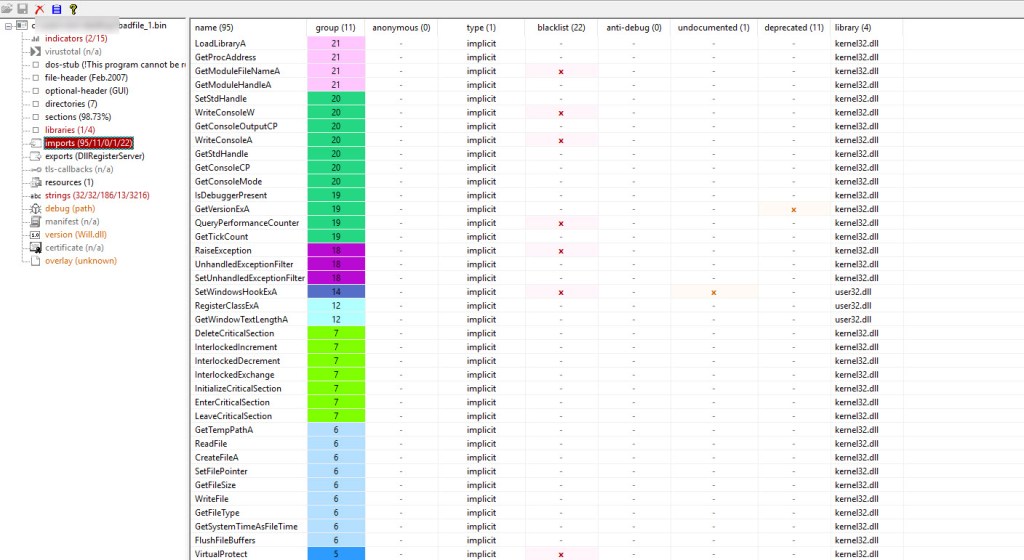
When I uploaded the new badfile_1.bin file to PeStudio, it was able to see additional information on the file.
The binary does have imports that can be used for malicious intent, but right now I don’t see anything that sticks out to be but the file called “Will.dll” and based on Virus Total the file has not been seen.
I am going to rename the file as an “.exe” and see if I can find anything when executing it in Any.Run.
The file did not show any suspicious activity, but Any.Run did consider the file to be malicious.
Any.Run Link: https://app.any.run/tasks/b52fa768-465f-402d-b65e-a31557cd5b32
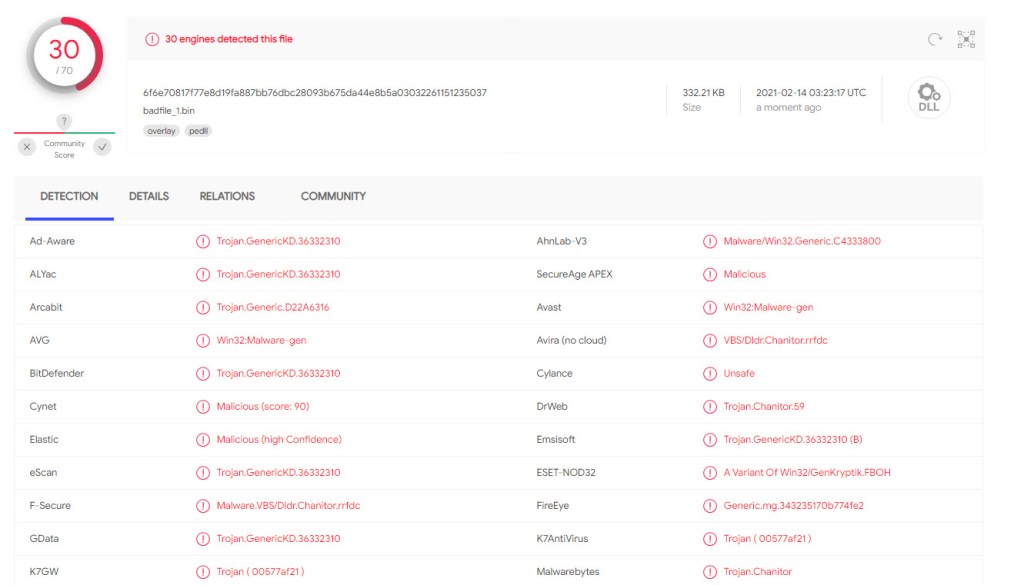
Let’s see what Virus Total says about the file.
Virus Total Link: https://www.virustotal.com/gui/file/6f6e70817f77e8d19fa887bb76dbc28093b675da44e8b5a03032261151235037/detection
Virus Total See the file as bad, also notice that the file has never been seen before.
My Conclusion:
If I have some time I will analyze the file “badfile_1.bin” and update this web page, but until now that is all I have for today. I hope you like how we analyzed the file and until next time.
Filename IOCs:
C:\Users\MyPc\Desktop\Builder_v6\Wh102yYa.tmp
C:\Users\MyPc\AppData\Local\Temp\Wh102yYa.tmp
File Hashes:
Badfile_.bin – 343235170b774fe2ab388dbdb59e4b46