Malicious File First Seen: 1/22/2021
2/6/2021 – Today I will be analyzing a ZLoader docm MS Word document.
Malware Bazaar Source: https://bazaar.abuse.ch/sample/409ed829f19024045d26cc5d3a06e15a097605e13ba938875eca054a7a4a30b1/
ZLoader Malware Download: https://bazaar.abuse.ch/download/409ed829f19024045d26cc5d3a06e15a097605e13ba938875eca054a7a4a30b1/
Sandbox Analysis: https://app.any.run/tasks/de75ee50-fd48-4416-b028-9daf81b115de/
Based on the Sandbox analysis there was no indication of URLs being accessed or files being created (assigned from the *.docm file, which is the file itself) in the temp directory.
Lets try an manually analysis this file to see if we can gather some IOC (Indicators of Compromise) from the malicious file.
Lets Get Started!!….
First lets unzip the file….
Command 1: 7z x -pinfected 409ed829f19024045d26cc5d3a06e15a097605e13ba938875eca054a7a4a30b1.zip
Command 2: mv 409ed829f19024045d26cc5d3a06e15a097605e13ba938875eca054a7a4a30b1.docm zloader.docm
NOTE: Command 1 corresponds to number 1, and Command 2 Corresponds to number 2, in the screen shot below.
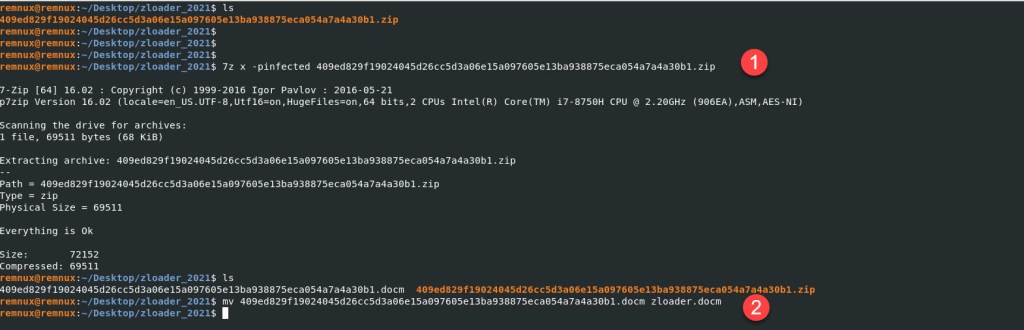
Using the OLEVBA tool shows me that the file is using some UserForm* type of OLE Stream. It also shows us some suspicious keywords that maybe malicious.
Command: olevba zloader.docm
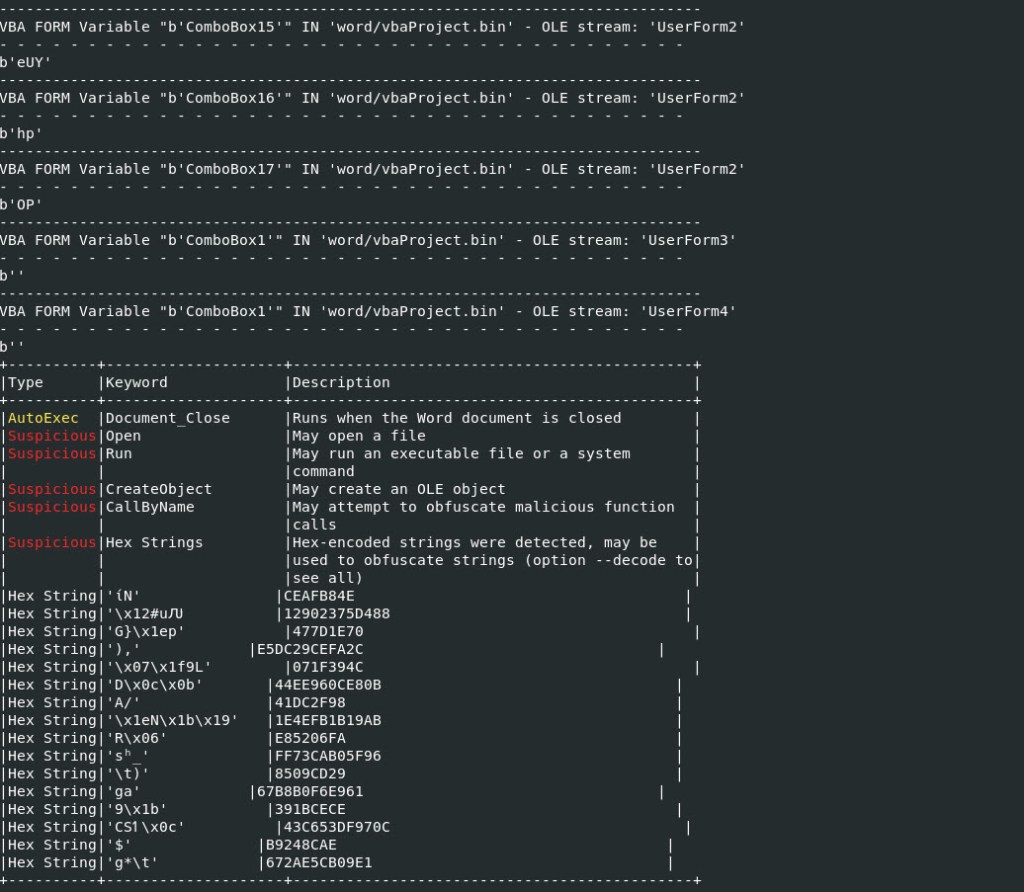
Lets see what Oledump.py shows us on this malicious document. This malicious files makes use of UserForm, which a window or dialog box within excel.

This time instead of going through the document and look at each one of the streams I am going to unzip the “DOCM” document. If you don’t know the newer extensions of Office documents are really zip files. For example: xlsx, docx, pptx, and docm.
They can actually be unzipped using the native windows unzipping or uncompress tool built into Windows OS.
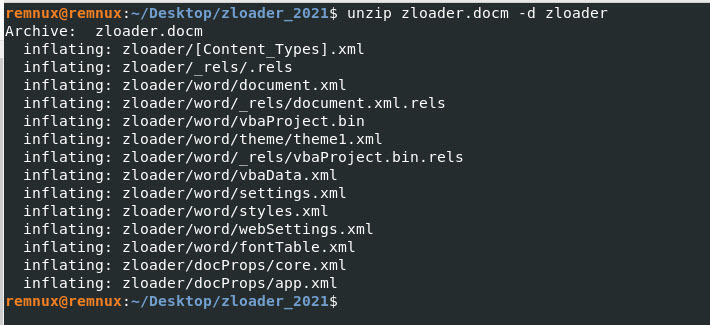
Command: unzip zloader.docm -d zloader
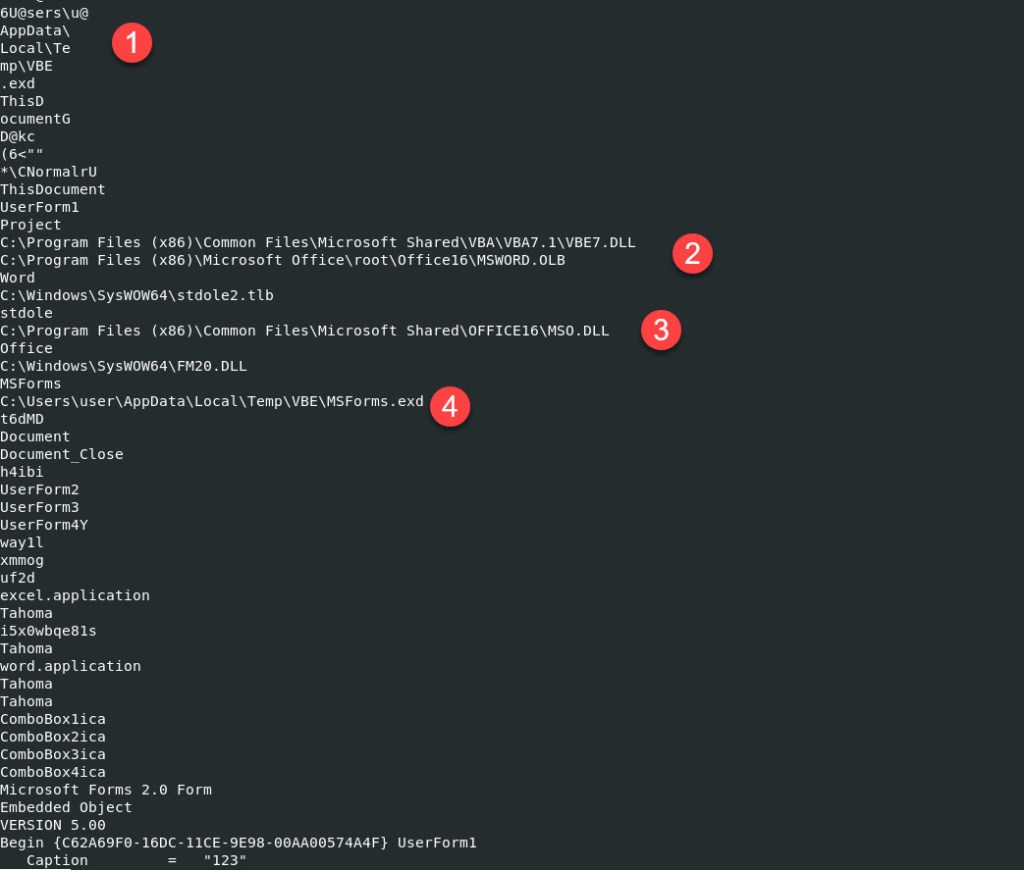
I will analyze the marcos in the vbaProject.bin file. Running the strings command piped with the more command I will go through snippets of the output.
Command: strings zloader/word/vbaProject.bin | more
Looking at the Number 1 we can see some type of potential file path and file creation “AppData\Local\Temp\VBE.exd”, we can also see at Number 2, some native files that can lead us to alert on false positive activity if we monitored this DLLs. At Number 4 23 can see the call or execution of a file “C:\Users\user\AppData\Local\Temp\VBE\MSForms.exd”
Instead of using the “more” command lets use the “grep” command and look for “http” strings, maybe we will find a URL.
Command: strings zloader/word/vbaProject.bin | grep http
Yes!!! We get an output of http being found in the binary file.
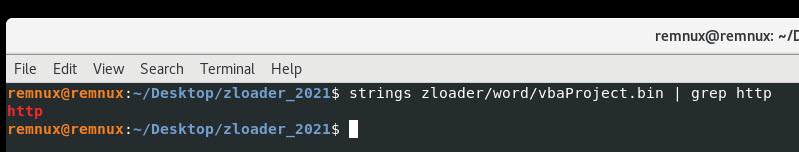
Lets look at a some lines of strings before and after finding http.
Command: strings zloader/word/vbaProject.bin | grep http -B15 -A15
Looking at the 15 lines before the http seems to be useless for us right now so lets focus on anything after http.
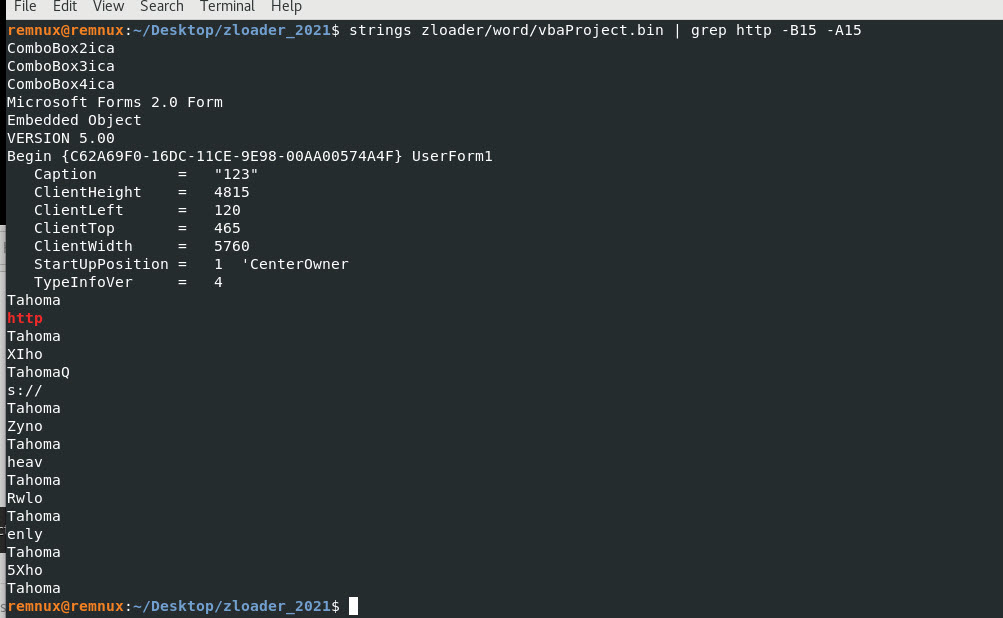
I am going to look at the next 30 lines of string information after identifying http.
Command: strings zloader/word/vbaProject.bin | grep http -A30
Something looks odd on this output. Looks like we may have random characters and some repeating characters… lets use Notepad++ to remove them.
We will remove the following characters: Tahoma, and everything ending with the letter “o”, and lets see what happens….
Lets start with everything after Tahoma first..

This is what we are left with after removing everything that ended with the letter “o”. Now lets remove “Tahoma” and line everything up into a single line.
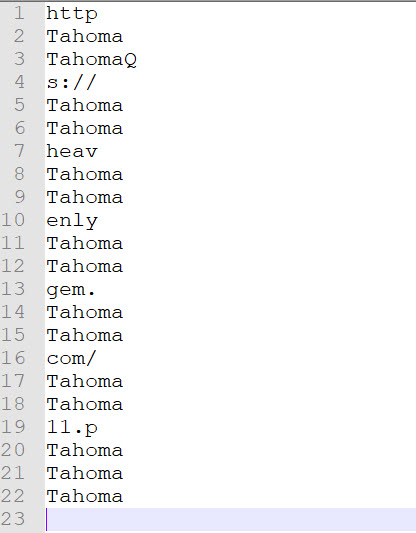
Here is our output.

We will remove the letter “Q” and line everything up now.
I will say that the file extension should be “.php” lets give it a try and run it on Blue Coat Site Reviewer and Any.Run
Based on Blue Coat Site Reviewer Analysis this website is suspicious.
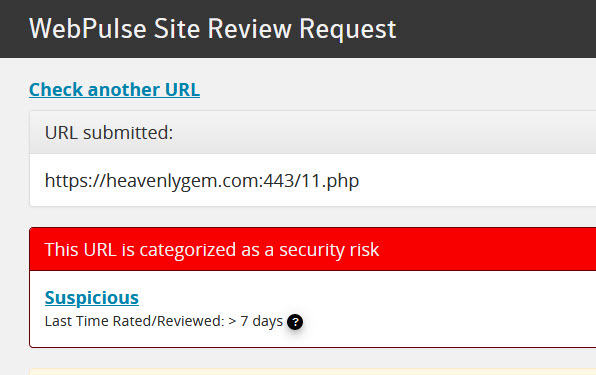
Any.Run did not consider this website malicious as you can tell from the link below the website does not download any malicious file, but it asks for you to pick a language and click on Go To website. Not sure what that is all about. I would still look out for communication to this website now or historically within your environment.
Any.Run Information: https://app.any.run/tasks/9f49db4a-5d83-4590-aaec-75d02185d4f8
My Conclusion:
In this document I was able to extract the URL that was being used by the malicious document that was not detected by Any.Run. If I am able to decode the VBA code I found, I will update this document.
Domain IOCs:
https[:]//heavenlygem[.]com/11.php
File Name IOC:
Not Available
Suspicious Path File Execution IOC:
Not Available